Situation: An organization has users that log into workstations interactively and also log into a Terminal Server with the same user account, but stricter policies are desired for the Terminal Server session than for the users’ interactive session with their own computer. Also, certain users (such as Administrators) should be exempt from these policies.
- ex: When a domain user logs on to Terminal Server, they do not have access to the Control Panel and cannot change the Desktop wallpaper; on their own machine these actions are allowed. Administrators that log on to the Terminal Server still must have access to the Control Panel and all other areas of the system.
Problem: Since users can only be contained in a single OU, and user policies assigned to OUs that contain only computers are not processed, it may seem that this is not possible without creating separate user accounts just for accessing the Terminal Server. Strict local policies could be used on the Terminal Server itself, but these would also apply to Administrators making the server difficult to manage.
Solution: Use loopback processing of group policy in conjunction with security filtering of certain GPOs to allow different user policies to be applied depending on what computer the user logs on to.
- In Active Directory Users and Computers, make sure that the Terminal Server is in its own OU just for Terminal Servers. If the Terminal Server is also a Domain Controller, a new OU can be created inside of the Domain Controllers OU so that domain controller policies are still applied as well.
- In the Group Policy Management MMC, create a new GPO called “Loopback” and link it to the Terminal Servers OU created in step 1.
- Edit the new Loopback policy to enable Loopback processing. The setting is under Computer Configuration -> Policies -> Administrative Templates -> Group Policy -> User Group Policy loopback processing mode. See example below:
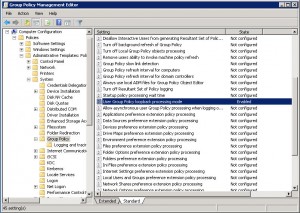
- Now create another GPO linked to the same Terminal Servers OU. This one will contain the user policies that will be in effect when users from another OU log on to a computer in this OU. Name it something like “Terminal Server Lockdown”, or whatever suits the situation.
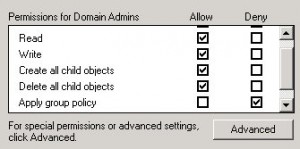
- Before editing this policy, it is important to set up some security filters first. Assuming you do not want this policy applied to Domain Administrators, perform the following steps:
- Edit this “Lockdown” policy just as you would any other user policy, making sure that you edit items in the “User” section, not the “Computer” section. Remove the Control Panel, lock the taskbar, customize Internet Explorer, etc.
- If everything went properly, this policy will be applied to any user that logs on to the Terminal Server (or any computer in the “Terminal Servers” OU) except those that are members of the Domain Admins group. If the policies do not immediately work, try running gpupdate /force when logged on to the server as a Domain User.
-n


Leave a Reply